- Home
- Prelims
- Mains
- Current Affairs
- Study Materials
- Test Series
Daily Current Affairs | 23rd May 2020
Certifying Quantum Entanglement: A step towards Quantum Security
Scientists from S. N. Bose National Centre for Basic Sciences (SNBNCBS), Kolkata, an autonomous institute of the Department of Science and Technology have developed a novel protocol to find out whether a pair of electrons is in an entangled state so that they can be safely used as resources for facilitating quantum information processing tasks. The protocol has been developed through theoretical and experimental analysis.
‘Quantum Mechanics’
 Quantum Technology
Quantum Technology
 Applications of Quantum Technology
Applications of Quantum Technology

 Quantum entanglement
Quantum entanglement
- It is a fundamental theory in physics which describes nature at the smallest – including atomic and subatomic – scales.
- At the scale of atoms and electrons, many of the equations of classical mechanics, which describe how things move at everyday sizes and speeds, cease to be useful.
- In classical mechanics, objects exist in a specific place at a specific time.
- However, in quantum mechanics, objects instead exist in a haze of probability; they have a certain chance of being at point A, another chance of being at point B and so on.
 Quantum Technology
Quantum Technology
- Quantum Technology is based on the principles of Quantum mechanics, that was developed in the early 20th century to describe nature in the small — at the scale of atomic and subatomic levels.
- The first phase of this revolutionary technology has provided the foundations of our understanding of the physical world, including the interaction of light and matter, and led to ubiquitous inventions such as lasers and semiconductor transistors.
- However, despite a century of research, the quantum world still remains mysterious and far removed from our experiences based on everyday life.
- Thereby, a second revolution is currently underway with the goal of putting properties of quantum mechanics in the realms of computing.
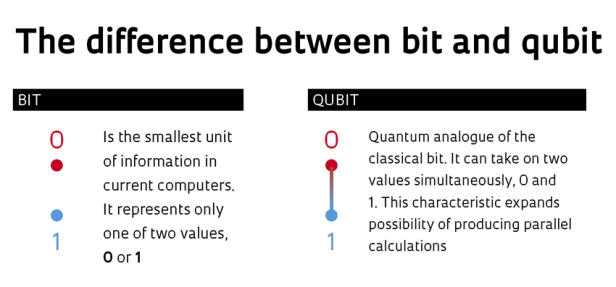
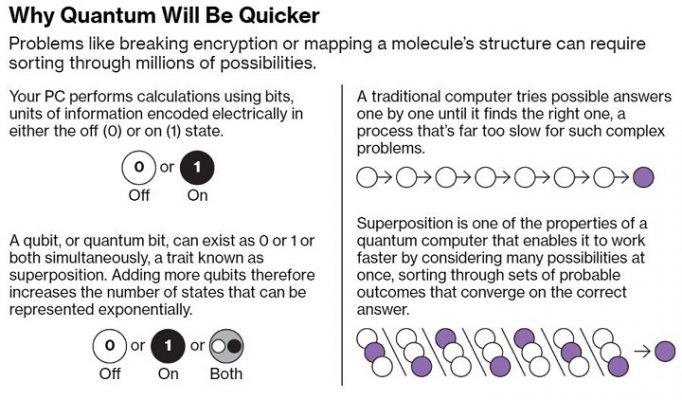
- Conventional computers process information in ‘bits’ or 1s and 0s, following classical physics under which our computers can process a ‘1’ or a ‘0’ at a time.
- Quantum computers compute in ‘qubits’ (or quantum bits). They exploit the properties of quantum mechanics, the science that governs how matter behaves on the atomic scale.
 Applications of Quantum Technology
Applications of Quantum Technology
- Secure Communication – China recently demonstrated secure quantum communication links between terrestrial stations and satellites. This area is significant to satellites, military and cyber security among others as it promises unimaginably fast computing and safe, unhackable satellite communication to its users.
- Research – It can help in solving some of the fundamental questions in physics related to gravity, black hole etc. Similarly, the quantum initiative could give a big boost to the Genome India project, a collaborative effort of 20 institutions to enable new efficiencies in life sciences, agriculture and medicine.
- Disaster Management – Tsunamis, drought, earthquakes and floods may become more predictable with quantum applications. The collection of data regarding climate change can be streamlined in a better way through quantum technology. This in turn will have a profound impact on agriculture, food technology chains and the limiting of farmland wastage.
- Pharmaceutical Industry – India’s interest in the pharmaceutical and healthcare industry is huge. Quantum computing could reduce the time frame of the discovery of new molecules and related processes to a few days from the present 10-year slog that scientists put in. For instance, tracking protein behaviour or even modelling new proteins with the help of quantum computers could be made easier and faster. Tackling chronic diseases like cancer, Alzheimer’s and heart ailments is a big possibility of the technology.

 Quantum entanglement
Quantum entanglement
- Quantum entanglement is one of the peculiarities of quantum mechanics, which makes phenomena such as quantum teleportation and super-dense coding possible.
- It is the physical phenomenon that occurs when a pair or group of particles is generated, interact, in a way such that the quantum state of each particle of the pair or group cannot be described independently of the state of the others. Entangled states are key resources to facilitate many quantum information processing tasks and quantum cryptographic protocols.
- However, entanglement is fragile and is easily lost during the transit of photons through the environment. Hence it is extremely important to know whether a pair of photons is entangled, in order to use them as resource.
- Verification of entanglement requires the use of measurement devices, but such devices may be hacked or compromised by eavesdroppers. Device-independent self-testing (DIST) is a method that can be used in order to overcome such a possibility.
- This method enables the verification of entanglement in an unknown quantum state of two photons without having direct access to the state, or complete trust in the measurement devices.
- The theory relies on the application of the quantum uncertainty principle while implementing full device independence is a difficult task.
- In several practical situations, one of the parties may be fully trusted, whereas, the other may not be trusted like in the case of server-client relationship in banking transactions. For such situations, quantum information theory enables one-sided DIST (1sDIST).
- Section 499 and 500 of Indian Penal Code,1860 deals with Criminal defamation.
- It prescribes two years’ imprisonment with or without fine for a person found guilty of defamation.
- Defamation is one of the recognized exceptions to the fundamental right to free speech and expression under Article 19(1)(a) of the Constitution.
- In Subramanian Swamy vs Union of India case, a bench of Justices Dipak Misra and P C Pant approved the Constitutional validity of sections 499 and 500 (criminal defamation) in the Indian Penal Code, underlining that an individual’s fundamental right to live with dignity and reputation “cannot be ruined solely because another individual can have his freedom”.
- The ruling noted that “the right to freedom of speech and expression is not an absolute right” and has to be “balanced with the right to reputation” which is protected under Article 21 of the Constitution”.
- The court held that criminalisation of defamation to protect individual dignity of life and reputation is a “reasonable restriction” on the fundamental right of free speech and expression. The judgment holds far-reaching implications for political dissent and a free press.
- In August 2016, the court also passed strictures on Tamil Nadu Chief Minister J Jayalalithaa for misusing the criminal defamation law to “suffocate democracy” and, the court said, “public figures must face criticism”. However, it also underscored that criticism was not defamation, the bench accepted their plea that a trial court must be “very careful” in scrutinizing a complaint before issuing summons in a criminal defamation case.
- Tathagata Satpathy, a member of Parliament belonging to the Biju Janata Dal, drafted a private member’s Bill entitled “The Protection of Speech and Reputation Bill, 2016”.
- The Bill sought to decriminalize defamation and remove the “chilling effect” of old provisions that throttle free speech and encourage censorship.
- The Bill sought to remove the criminal provisions while guarding the right to reputation with stronger, more effective remedies for civil relief, including apologies, corrections and retractions, and the award of reasonable damages.
- The Bill also attempted to set the maximum claim limits and to bar governments, local bodies and other institutions, exercising statutory functions, from filing suits for defamation. However, the Bill has not been passed by any house of Parliament yet.
- In 2019, the IIT Guwahati scientists found that application of a low-voltage, safe electrical field can reduce the formation and accumulation of toxic neurodegenerative molecules that cause short-term memory loss in Alzheimer’s disease.
- They found that external electric/magnetic field modulates the structure of these peptide molecules, thereby preventing aggregation.
- Upon exposure to electric field, we could retard the degeneration of nerve cells to an extent of 17–35%. Objectively, this would translate to about 10 years delay in the onset of the disease.
- Working further in this area, the scientists explored the possibility of using ‘Trojan peptides’ to arrest aggregation of these neurotoxic molecules. The idea of using ‘Trojan peptide’ comes from mythological “Trojan Horse” used as subterfuge by the Greeks in the battle of Troy.
- The researchers have designed Trojan peptides by adopting a similar approach of ‘deceit’ to impede the aggregation of the amyloid peptide, arrest the formation of toxic fibrillar assemblies, and reduce poisoning of nerve cells that leads to memory loss.
- It is an irreversible and progressive brain disorder.
- The disease slowly destroys memory, thinking ability and the capability to carry out simple tasks.
- The possibility of Alzheimer’s increases as the age of the population increases.
- Nearly 50 million people are affected by the disease and the number is expected to increase. China has the highest Alzheimer’s affected the population in the world.
- Sound travels in the form of waves which are emitted outwards from its source. In air, the speed of these waves depends on a number of factors, such as the temperature of the air and altitude. From a stationary source, such as a television set, sound waves travel outwards in concentric spheres of growing radii.
- When the source of sound is moving – e.g, a truck– the successive waves in front of the truck get closer together, and the ones behind it spread out. This is also the cause of the Doppler effect– in which bunched waves at the front appear at a higher frequency to a stationary observer, and spread out waves that are behind are observed at a lower frequency.
- As long as the source of the sound keeps moving slower than the speed of sound itself, this source– say a truck or a plane – remains nested within the sound waves that are travelling in all directions.
- When an aircraft travels at supersonic speed – meaning faster than sound (>1225 kmph at sea level) – the field of sound waves moves to the rear of the craft. A stationary observer thus hears no sound when a supersonic flight approaches, since the sound waves are at the rear of the latter.
- At such speeds, both newly created as well as old waves, are forced into a region at the aircraft’s rear called a ‘Mach cone’, which extends from the craft and intercepts the Earth in a hyperbola-shaped curve, and leaves a trail called the ‘boom carpet’. The loud sound that is heard on the Earth when this happens is called a ‘sonic boom’.
- When such aircraft fly at a low altitude, the sonic boom can become intense enough to cause glass to crack or cause health hazards. Overland supersonic flights have thus been banned in many countries.
- When first created by the Second Committee of the UN General Assembly in late 1993, 29 December (the date of entry into force of the Convention of Biological Diversity), was designated The International Day for Biological Diversity.
- In December 2000, the UN General Assembly adopted 22 May as IDB, to commemorate the adoption of the text of the Convention on 22 May 1992 by the Nairobi Final Act of the Conference for the Adoption of the Agreed Text of the Convention on Biological Diversity.
- This was partly done because it was difficult for many countries to plan and carry out suitable celebrations for the date of 29 December, given the number of holidays that coincide around that time of year.
- The Convention on Biological Diversity (CBD), a legally binding treaty to conserve biodiversity has been in force since 1993. It has 3 main objectives – The conservation of biological diversity; The sustainable use of the components of biological diversity, and; The fair and equitable sharing of the benefits arising out of the utilisation of genetic resources.
- Nearly all countries have ratified it (notably, the US has signed but not ratified).
- The CBD Secretariat is based in Montreal, Canada and it operates under the United Nations Environment Programme.
- The Parties (Countries) under Convention of Biodiversity (CBD), meet at regular interval and these meetings are called Conference of Parties (COP).
- Pursuant to the Convention on Biodiversity, India enacted the Biological Diversity Act in 2002, and notified Biological Diversity Rules in 2004, to give effect to the provisions of this Convention. The Act is implemented through a three-tiered institutional structure at the national, state and local levels.
- The National Biodiversity Authority (NBA) has been set up in October, 2003 in Chennai. As per Section 8(4) of the Act, the NBA consists of a Chairperson, five non-official and ten ex-officio members to be appointed by the Central Government to represent various Ministries.
- The vision of NBA is the conservation and sustainable use of India’s rich biodiversity and associated knowledge with peoples participation, ensuring the process of benefit sharing for well being of present and future generations.
- The mission of NBA is to ensure effective implementation of Biological Diversity Act, 2002 and the Biological Diversity Rules 2004 for conservation of biodiversity, sustainable use of its components and fair and equitable sharing of benefits arising out of utilisation of genetic resources.
- The NBA inter-alia deals with all matters relating to requests for access by foreign individuals, institutions or companies, and transfer of results of research to any foreigner.
- The State Biodiversity Boards (SBBs) constituted by the State Governments deal with all matters relating to access by Indians for commercial purposes.
- The institutions of self-governments are required to set up Biodiversity Management Committees (BMCs) in their respective areas for conservation, sustainable use, documentation of biodiversity and chronicling of knowledge related to biodiversity.









 Latest News
Latest News
 General Studies
General Studies